Report Generation
Once the Threat Analysis process is completed, we can generate a full documentation, including all the analysis outcomes.
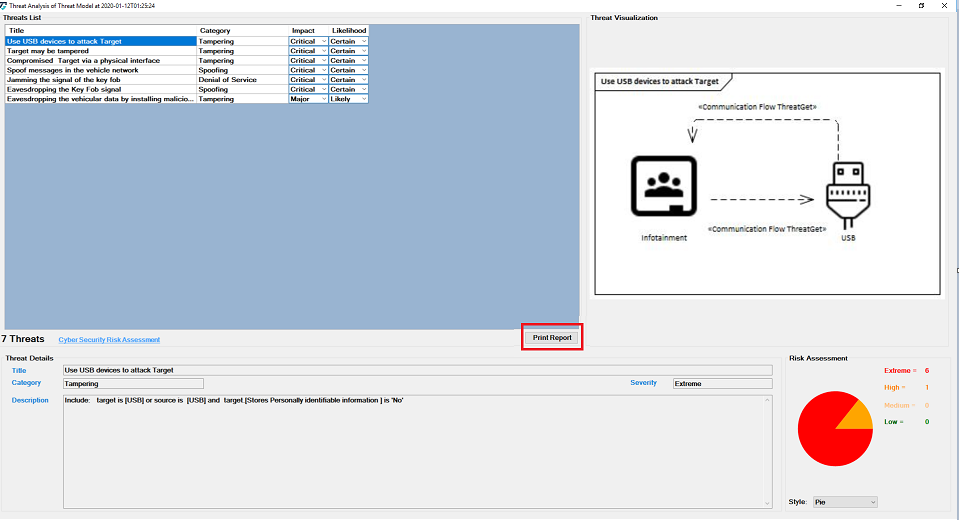
To generate a threat analysis report click on Print Report button on the Threat Analysis tab as shown below.
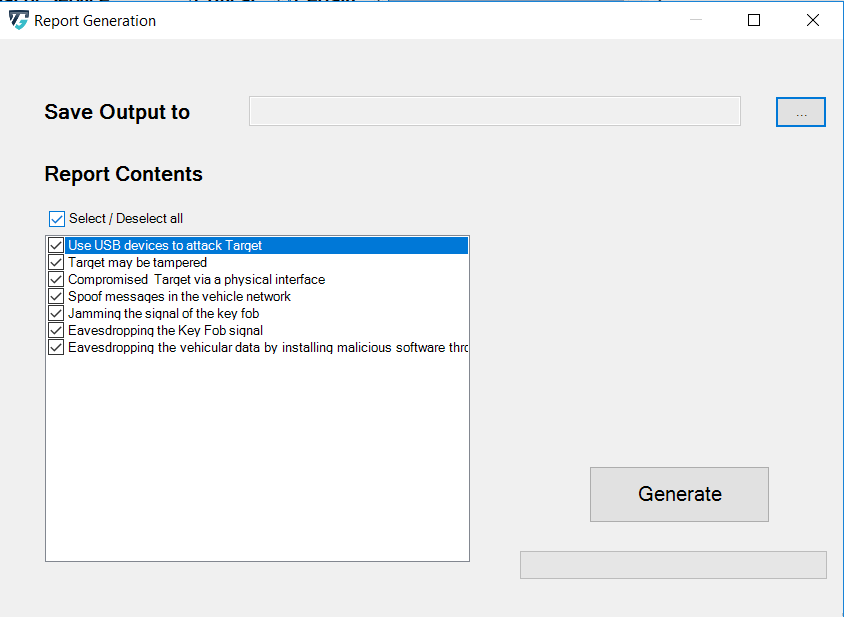
Click on the symbol ... adjacent to Save Output to, select the destination file path to save the report as shown below.
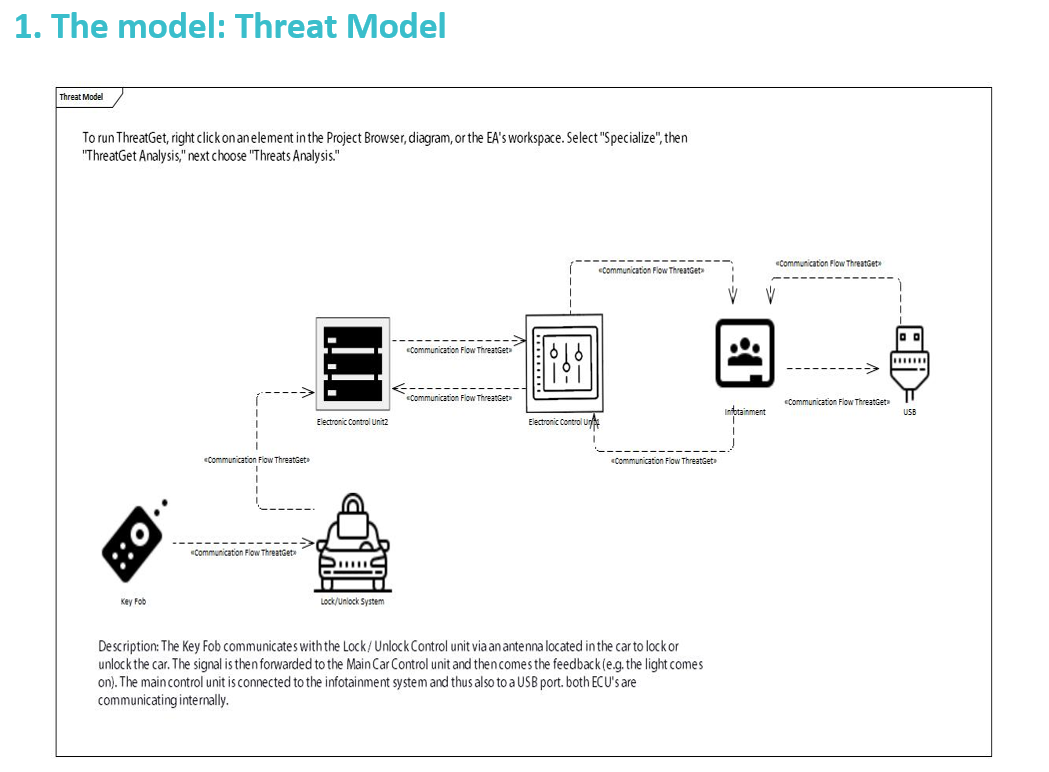
After you have selected the desired path, you can now specify whether you want to have all or part of the analysis in a report. By default, all threats found are selected. You can deselect individual threats by clicking the box. You can also use Select/deselect all to select or deselect all elements at once.
Click on Generate, to generate the report, as shown below.

The report's main page includes the ThreatGet logo, the version, the path of the EA file (i.e. where the project is saved), the author, and the timestamp, as shown in the picture.

The Table of Contents is described on the secound page, showing the main parts of the generated report, as shown below.
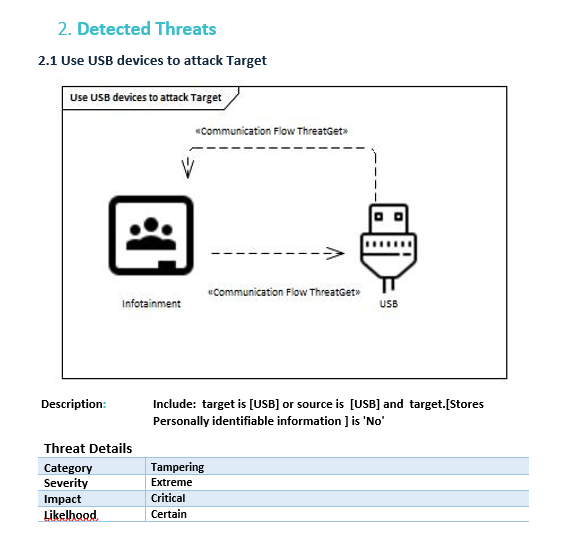
You will find the selected threats identified according to the Threat Analysis. The title, diagram, definition and details (i.e., category, severity, impact, and likelihood) of each threat are defined.
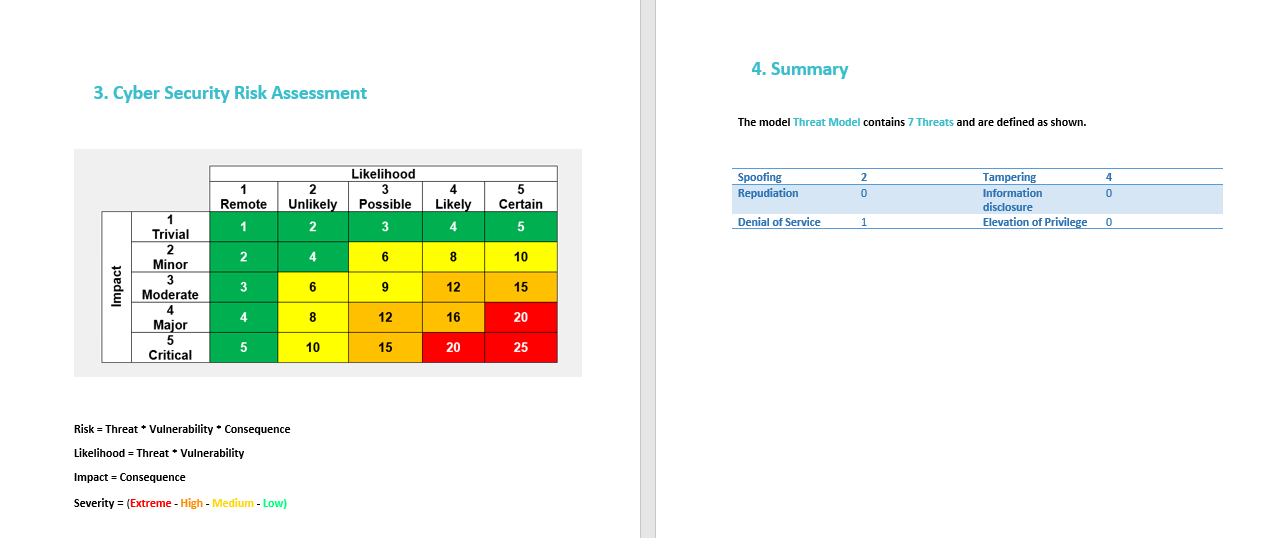
The Cyber Security risk assessment is summarized in the last two pages. It shows how the risk, likelihood, impact & severity are calculated. The summary of the categories is then on the last page of the report.